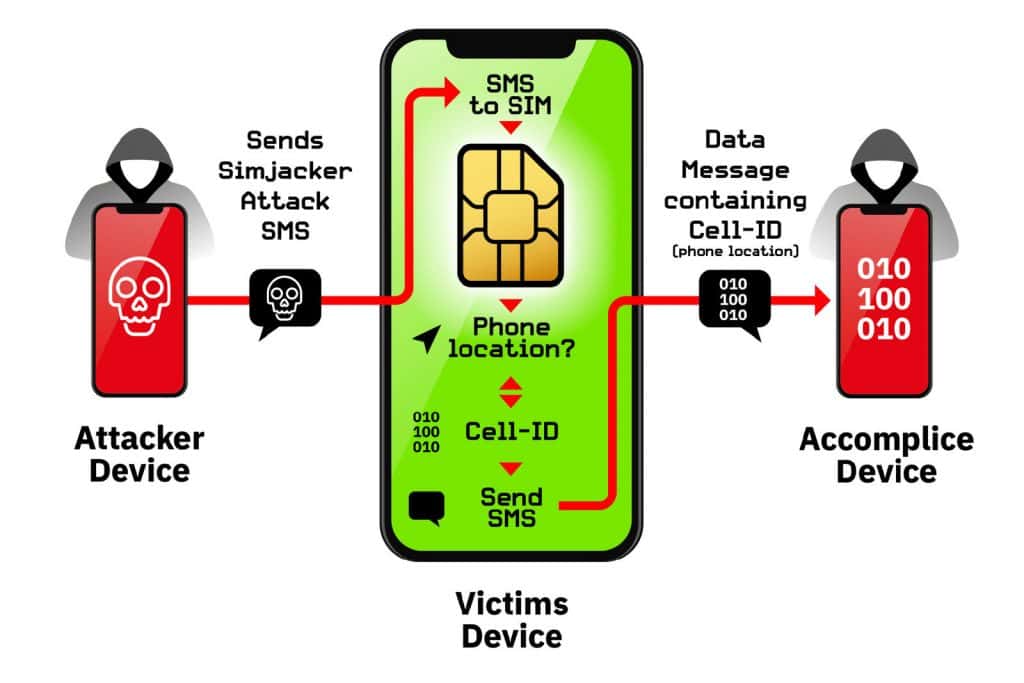
Simjacker theoretically affects most phones.
In a few cases,your SIM card may pose more of a security risk than your phone’s software. AdaptiveMobile Security researchers say they’ve discovered a new vulnerability, nicknamed Simjacker, that’s being used to surveil people’s devices by an unnamed surveillance company. The technique sends SMS messages containing instructions for an old S@T Browser app supported on some carriers’ SIM cards. Where S@T was originally intended to launch browsers, play sounds or otherwise trigger common actions on phones, Simjacker uses it to obtain location info and IMEI numbers that are later sent to an “accomplice device” (again using SMS) that records the data.
Crucially, the approach is silent. While it does use SMS, you won’t get notifications. An intruder can obtain frequent updates without giving away their activity. The exploit is also device-agnostic, and has been used against iPhones, numerous brands of Android phones and some SIM-equipped Internet of Things devices.
And it’s not just a theoretical exercise. The surveillance company has reportedly been using Simjacker in 30-plus countries (mainly in the Middle East, North Africa, Asia and eastern Europe) for a minimum of two years. While most targets were ‘only’ checked a few times per day over long stretches of time, a handful of people were targeted hundreds of times over the space of a week — 250 in the case of the most prominent target. It’s not believed to be a mass surveillance campaign, but AdaptiveMobile also hasn’t said whether this was being used for tracking criminals or more nefarious purposes, like spying on political dissidents. The company is mounting a “highly sophisticated” operation, AdaptiveMobile said.
It should be possible for networks to thwart these attacks. Simjacker is sending code rather than everyday text, so it should be feasible to block the code. It may be difficult to coordinate that response, though, when the affected countries have a total population of a billion. And while you’re not likely to be targeted by this particular organization, there’s nothing precluding a similarly capable attacker from launching a wider campaign. It may be a long while before you can assume your SIM isn’t a potential weakness.


